For organisations today, suffering a serious security breach involving privileged access is no longer a question of if, but when. This report discusses the current threats from privileged insiders and vendors and provides recommendations for managing, controlling, and monitoring the privileged access organisations grant to their systems and data.
Library
A DevSecOps culture is a must to maintain speed, agility and innovation while simultaneously meeting regulations and staying ahead of attacks. Learn how to bake it into your technology’s DNA from Day 1.
-
George Gerchow VP of Security and Compliance, Sumo Logic

The EU General Data Protection Regulation (GDPR) deadline is 25 May, 2018. If you think you’re immune from its impact, think again.
-
Stephen Twynam Senior Sales Engineer, Citrix

-
Lawrence Dietz General Counsel and Managing Director, Information Security, TAL Global

Whether it is creating a clear roadmap or strengthening relationships between team members, integrating an effective software security strategy into developing, managing or purchasing software is vital.
-
- Download
Fifteen years since the original Agile Manifesto was published, it still holds strong as one of the most popular methodologies for continuous delivery. However, one vital aspect of software development - security - is often left out of the procedure.
-
- Download
A new data protection framework for the whole of the European Union seeks to create a harmonised regulation that is fit for purpose in today’s fast-moving IT, data and compliance landscape. Yet despite the fact that the proposed new rules will be implemented on 25th May 2018, IT professionals are worryingly unprepared for the change.
-
- Download
One way cybercriminals obtain the resources and connections they need to engage in their activities is through the Internet underground or “dark web.” Definitions of the Internet underground may vary, but to Secureworks, it means the collection of Internet forums, digital shop fronts and chat rooms that cybercriminals use to form alliances, trade tools and techniques, and sell compromised data that can include banking details, personally identifiable information and other content.
-
Mike McLellan Senior Security Researcher, Secureworks Counter Threat Unit™ (CTU)MM
Last year, over $80 billion was spent on cyber security, yet two-thirds of organisations were still breached. The reason? 81% of data breaches involved weak, default or stolen passwords.
-
John Rudolph Principle consultant, Verizon

-
Corey Williams Senior Director of Products and Marketing, Centrify

It seems that no matter what we do, there will always be a new strain of malware designed to give CISOs grief. It might be called Wanna Cry, Pytra or any of thousand different names but malware keeps evolving for a simple reason — it works.
-
Candace Worley Vice President and Chief Technical Strategist, McAfee


Is your email system offering an easy route into your network for Ransomware?
Your email system is usually your weakest point of entry for ransomware attackers with 98% of phishing malware entering via email. How can you close this backdoor to your systems and avoid becoming a victim? Listen to our webinar to identify your weakspots – and discover how to strengthen them.
-
Steven Malone Director of Product Management for security services, Mimecast

It is no exaggeration that enterprises can run in average 25 security products concurrently, as it is the case with financial services organisations, according to research firm Ovum. And yet sometimes, 25 products can be as good as zero.
-
Gil Barak Co-Founder and Chief Technology Officer, Secdo

-
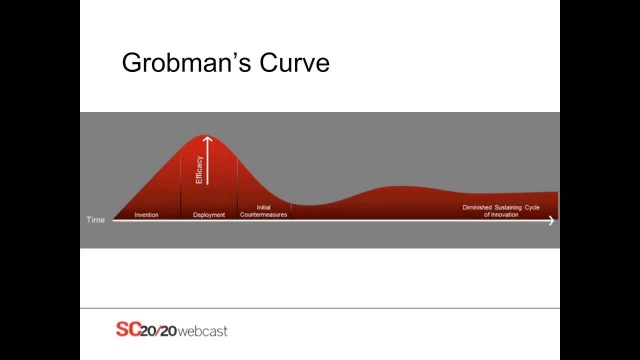
Golan Ben-Oni Global Chief Information Officer, IDT Corporation
An error occurred trying to play the stream. Please reload the page and try again.
CloseSign up benefits
Registering with SC Media is 100% free. Join tens of thousands of cybersecurity leaders today and gain access to the latest analysis shaping the global infosec agenda.
- Weekly newsletters featuring industry-leading insight
- Access to free cyber expert webinars and videos
- Privileged viewership of special reports, such as the Annual Cyber Salary Survey and Women of Influence








 play_arrow
play_arrow
 play_arrow
play_arrow





